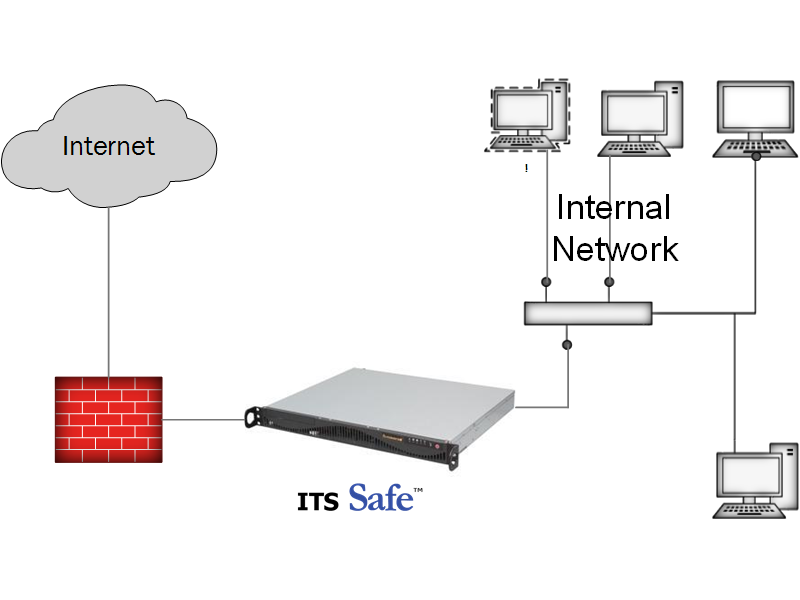
ITS Safe Security Appliance
ITS SafeTM Security Appliance.
The ITS SafeTM security appliance detects and blocks unwanted activities inside your network that firewalls and virus scanners simply can’t stop.
Blocking the BAD Activities.
 ITS Safe does not wait until a computer is hacked or breached, instead we
work on active traffic thus enabling the protection of all devices within the
network. ITS Safe blocks unwanted communications with foreign countries and the
dark web. It also blocks unregistered IP addresses, hijacked IP addresses, the
TOR network, and the user interface will allow the blocking of specific
websites during specific times or permanently.
ITS Safe does not wait until a computer is hacked or breached, instead we
work on active traffic thus enabling the protection of all devices within the
network. ITS Safe blocks unwanted communications with foreign countries and the
dark web. It also blocks unregistered IP addresses, hijacked IP addresses, the
TOR network, and the user interface will allow the blocking of specific
websites during specific times or permanently.
The ITS Safe security appliance monitors active traffic, and predetermined configuration rules, as well as other settings which we control to enable safe communications, restoring security to the environment.
Because no virus scanner can catch 100% of all known viruses, the virus detection methodology is a broken technology with empty promises. ITS Safe enables security teams or users to modify their configuration and affect security for the entire enterprise.
Easy to use integration into your environment
ITS Safe is the comprehensive tool used to get in front of the hackers, instead of waiting until they have succeeded. This is a huge improvement over SPLUNK, SIEM and Virus scanners which rely on definitions of activities which have already occurred. This process may take months or more to fine-tune. Using ITS Safe, we can identify attacks in progress and block them before they are effective.
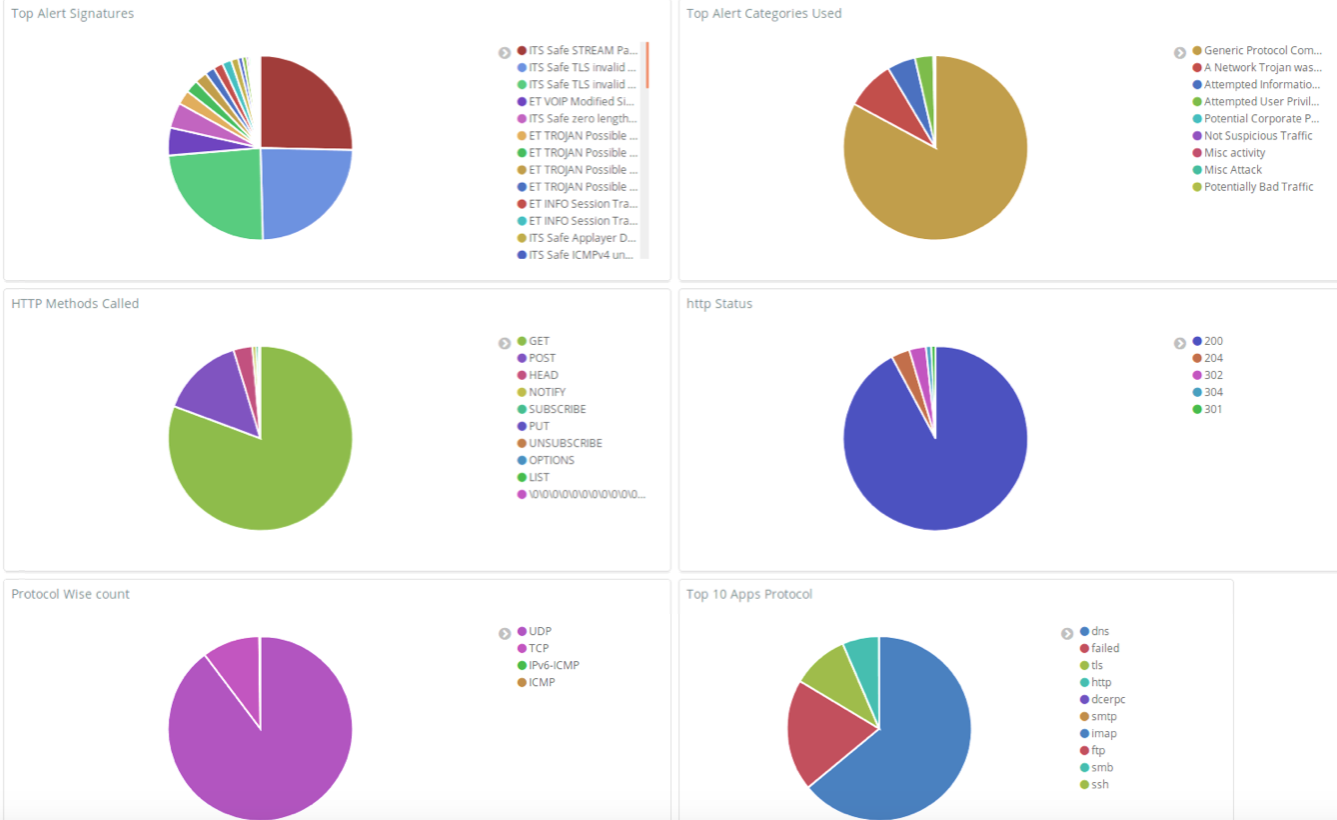
Where does your network traffic go?
Much of what we do with our computers has a mystery for many of us. While what we expect to happen with our computers is not necessarily what is occurring in reality. Here is a List of the Countries which was identified with the ITS Safe Security Appliance over a period of one week.

Be honest now, with the list above, How many countries do you want to talk with?
What's inside of your Network?
How fast is your Internet Connection? Gone are the days when we could detect Malicious activity within our networks, because the speed of our networks has increased significantly.
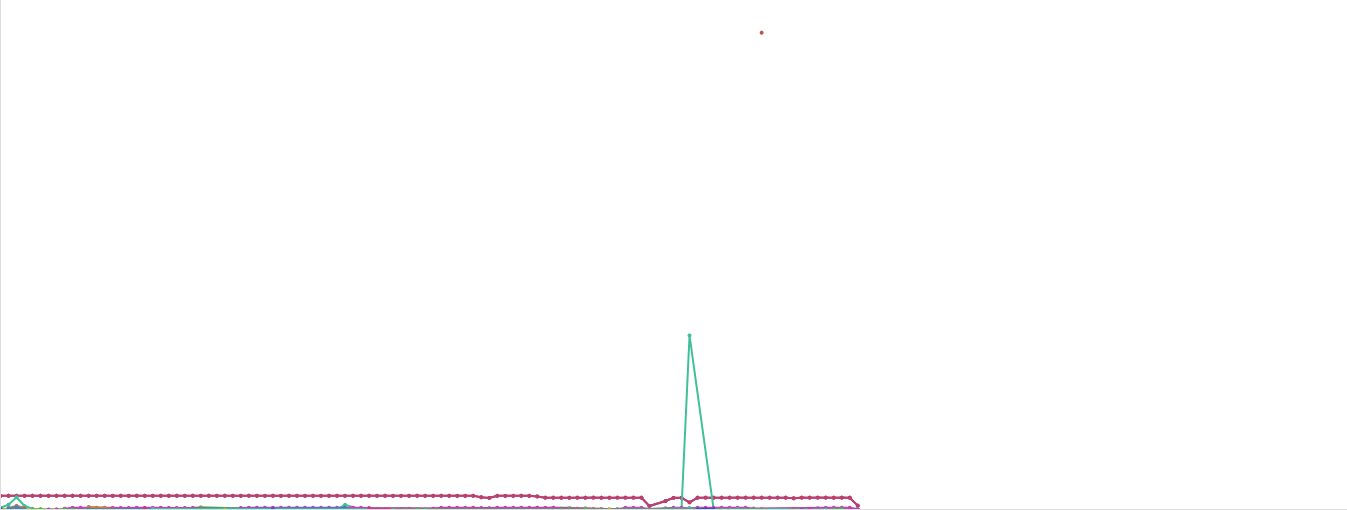
Does your existing solution identify abnormal network traffic making it easy to see?
Stopping the Hackers before they succeed
Much of the deployed technology today is based on a reactive stance, trying to indicate the severity of what has already occurred. The ITS SafeTM security appliance offers complete transparency about activities occurring within your Internet NOW and it enables you to control who you communicate with at any given point in time.
IT Security has tremendous experience in the various technologies used by business, government and consumers designed to use the Internet safely. While government and businesses try to meet compliance guidelines, our stance on cyber security is that being compliant does not make you secure. The ONLY way to be secure is to be proactive because it is 10,000 times less costly to prevent a breach than recover from one.




