ITS Safe Security appliance
 The
ITS SafeTM security appliance
detects and blocks unwanted activities inside your network that firewalls and
virus scanners simply can’t stop. ITS Safe does not wait until a computer is hacked
or breached, instead we work on active traffic thus enabling the protection of
all devices within the network. ITS Safe Product Description.
The
ITS SafeTM security appliance
detects and blocks unwanted activities inside your network that firewalls and
virus scanners simply can’t stop. ITS Safe does not wait until a computer is hacked
or breached, instead we work on active traffic thus enabling the protection of
all devices within the network. ITS Safe Product Description.
Active Defense
 Active
DefenseTM implements a layered approach to Unix/Linux security. Layered
security provides the best protection for the Network as well as the
Applications on the servers. While other companies want to implement an
off the shelf solution to fit all needs (as in a 'One Size FITS ALL!" approach), our Active DefenseTM and the
use of Layers, and multipe configurations to provide a customized solution, for Maximum protection.
Active
DefenseTM implements a layered approach to Unix/Linux security. Layered
security provides the best protection for the Network as well as the
Applications on the servers. While other companies want to implement an
off the shelf solution to fit all needs (as in a 'One Size FITS ALL!" approach), our Active DefenseTM and the
use of Layers, and multipe configurations to provide a customized solution, for Maximum protection.
Code Dx
 Code Dx® 2.0 is a software vulnerability management system
that consolidates and normalizes software vulnerabilities detected by
multiple static application security testing (SAST) and dynamic application security testing
(DAST) tools, as well as the results of manual code reviews. Its visual
analytics accelerate the finding, triage, prioritizing and fixing of
software vulnerabilities to dramatically expedite remediation. Let our professionals engage your organization for results that make a difference in your overall security.
Code Dx® 2.0 is a software vulnerability management system
that consolidates and normalizes software vulnerabilities detected by
multiple static application security testing (SAST) and dynamic application security testing
(DAST) tools, as well as the results of manual code reviews. Its visual
analytics accelerate the finding, triage, prioritizing and fixing of
software vulnerabilities to dramatically expedite remediation. Let our professionals engage your organization for results that make a difference in your overall security.
Clean Content
 Clean
Content is our answer to eliminating Viruses, spyware, crimeware and
unwanted content from the internet. Clean Content also scans the web
sites before you visit them to review the content on the page, before
you visit it. You have control on what you can see, you have control on
how much of the internet you will permit in your home or office. This is
your chance to put parental (or employer) controls where it is needed
most.
Clean
Content is our answer to eliminating Viruses, spyware, crimeware and
unwanted content from the internet. Clean Content also scans the web
sites before you visit them to review the content on the page, before
you visit it. You have control on what you can see, you have control on
how much of the internet you will permit in your home or office. This is
your chance to put parental (or employer) controls where it is needed
most.
Clean Content is our latest addition to the Active DefenseTM security suite.
Server Admin
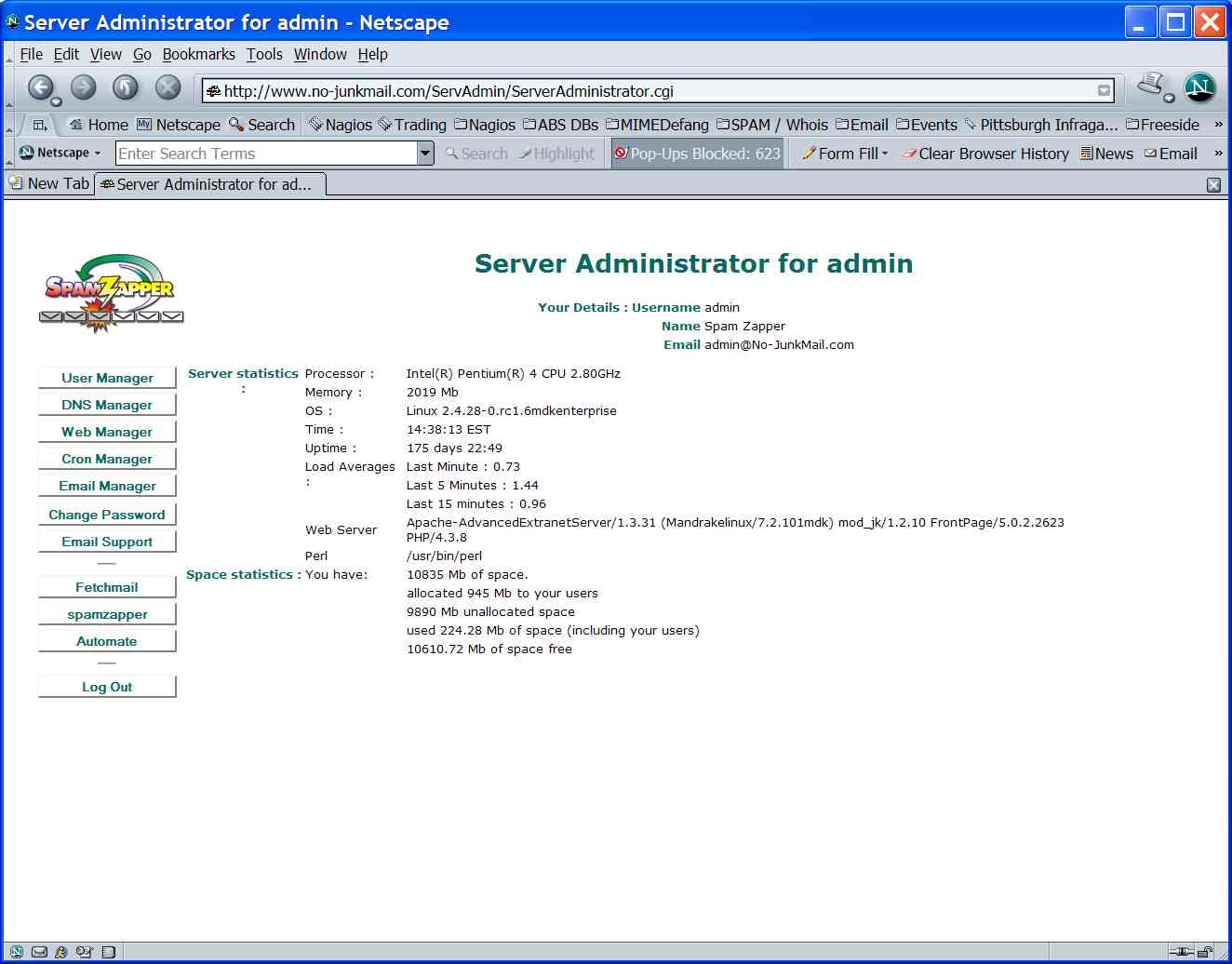 Our
server administrator is a GUI based administration tool which was
developed to support multiple servers, ISPs, or Web Hosting Facilities.
Typically the duplication of services across two or more servers is not a
simple task to manage.
Our
server administrator is a GUI based administration tool which was
developed to support multiple servers, ISPs, or Web Hosting Facilities.
Typically the duplication of services across two or more servers is not a
simple task to manage.
Our server administration tool makes it simple to duplicate services
for hosting, email, DNS and other administration functions. The server
administrator is based upon an internal database which is secured from
internet access.
Administration is based on a hierarchial association which permits
the Site Owner ultimate control, and each of the customers can then
become an administrator for their own group, or additional customers
that they can also control.
SpamZapper®

SpamZapper
® eliminates Spam, while other products and services will only filters
email. Our Email security solution (backed with the protection of our
Active Defense™) has proven to eliminate the hacker attacks on your
firewall and email server. Use our email hosting service if your
internet connection is being attacked. We'll block the hackers and put
an end to the attacks on your internet connection, almost immediately.
No one else makes this claim.
Server Safe
 Server
SafeTM is our layered security implementation which provides the
flexibility of a adaptive Firewall, and an IPS solution protecting your
environment from unwanted intrusions. Now we can protect Internet based
servers with the intelligence for detecting and repelling the attacks as
they start.
Server
SafeTM is our layered security implementation which provides the
flexibility of a adaptive Firewall, and an IPS solution protecting your
environment from unwanted intrusions. Now we can protect Internet based
servers with the intelligence for detecting and repelling the attacks as
they start.
Our customers know the value of protecting their servers. Server
Safe is today's solution for implementing improved secutiy for your
servers.
Strategically placing firewalls in your network is no longer a
complete solution for protecting your network. That's where Server Safe
will protect your valuable server assets, improving their ability to
work.
Wireless Security
 Remember
the 45 Million Credit Cards which were stolen from TJ Maxx (TJX), our
Wireless Security tools would have prevented the event in it's entirety.
Remember
the 45 Million Credit Cards which were stolen from TJ Maxx (TJX), our
Wireless Security tools would have prevented the event in it's entirety.
Our Wireless security tool prevents hackers from gaining access into
your network. It also prevents your employees from gaining access to an
outside wireless access point, which makes your network vulnerable to
infections from outside your network.
IT Security network designers can develop a strategy for small businesses to
global corporations. Small businesses will generally need one or two
devices to protect their operations, while larger companies will need an
Enterprise Management console which will consolidate all of the sensors
for your facility.
CimTrak

CimTrak is an advanced, file integrity monitoring tool that
offers a holistic approach to change and configuration management in the IT
environment. With the ability to monitor
a wide variety of systems including servers, workstations, network devices, databases,
and VMware ESXi hosts for changes, CimTrak can offer protection to your entire
network. Whether used to detect malware that may slip through traditional
defenses, identification of internal threats or for compliance with regulations
such as PCI-DSS, HIPAA, and FISMA, CimTrak keeps you secure and in a state of
continuous compliance.
Contact us for a demo or pricing.
Solutions for you!
IT Security is focused on delivering the best security to meet the needs of their clients. We take great pride in helping organizations implement better security practices and controls, BEFORE a breach occurs. Take a look at our experience, we think that it speaks for itself.

 The
ITS SafeTM security appliance
detects and blocks unwanted activities inside your network that firewalls and
virus scanners simply can’t stop. ITS Safe does not wait until a computer is hacked
or breached, instead we work on active traffic thus enabling the protection of
all devices within the network.
The
ITS SafeTM security appliance
detects and blocks unwanted activities inside your network that firewalls and
virus scanners simply can’t stop. ITS Safe does not wait until a computer is hacked
or breached, instead we work on active traffic thus enabling the protection of
all devices within the network.  Active
DefenseTM implements a layered approach to Unix/Linux security. Layered
security provides the best protection for the Network as well as the
Applications on the servers. While other companies want to implement an
off the shelf solution to fit all needs (as in a 'One Size FITS ALL!" approach), our Active DefenseTM and the
use of Layers, and multipe configurations to provide a customized solution, for Maximum protection.
Active
DefenseTM implements a layered approach to Unix/Linux security. Layered
security provides the best protection for the Network as well as the
Applications on the servers. While other companies want to implement an
off the shelf solution to fit all needs (as in a 'One Size FITS ALL!" approach), our Active DefenseTM and the
use of Layers, and multipe configurations to provide a customized solution, for Maximum protection. Code Dx® 2.0 is a software vulnerability management system
that consolidates and normalizes software vulnerabilities detected by
multiple
Code Dx® 2.0 is a software vulnerability management system
that consolidates and normalizes software vulnerabilities detected by
multiple  Clean
Content is our answer to eliminating Viruses, spyware, crimeware and
unwanted content from the internet. Clean Content also scans the web
sites before you visit them to review the content on the page, before
you visit it. You have control on what you can see, you have control on
how much of the internet you will permit in your home or office. This is
your chance to put parental (or employer) controls where it is needed
most.
Clean
Content is our answer to eliminating Viruses, spyware, crimeware and
unwanted content from the internet. Clean Content also scans the web
sites before you visit them to review the content on the page, before
you visit it. You have control on what you can see, you have control on
how much of the internet you will permit in your home or office. This is
your chance to put parental (or employer) controls where it is needed
most. Our
server administrator is a GUI based administration tool which was
developed to support multiple servers, ISPs, or Web Hosting Facilities.
Typically the duplication of services across two or more servers is not a
simple task to manage.
Our
server administrator is a GUI based administration tool which was
developed to support multiple servers, ISPs, or Web Hosting Facilities.
Typically the duplication of services across two or more servers is not a
simple task to manage.
 Server
SafeTM is our layered security implementation which provides the
flexibility of a adaptive Firewall, and an IPS solution protecting your
environment from unwanted intrusions. Now we can protect Internet based
servers with the intelligence for detecting and repelling the attacks as
they start.
Server
SafeTM is our layered security implementation which provides the
flexibility of a adaptive Firewall, and an IPS solution protecting your
environment from unwanted intrusions. Now we can protect Internet based
servers with the intelligence for detecting and repelling the attacks as
they start.  Remember
the 45 Million Credit Cards which were stolen from TJ Maxx (TJX), our
Wireless Security tools would have prevented the event in it's entirety.
Remember
the 45 Million Credit Cards which were stolen from TJ Maxx (TJX), our
Wireless Security tools would have prevented the event in it's entirety.




