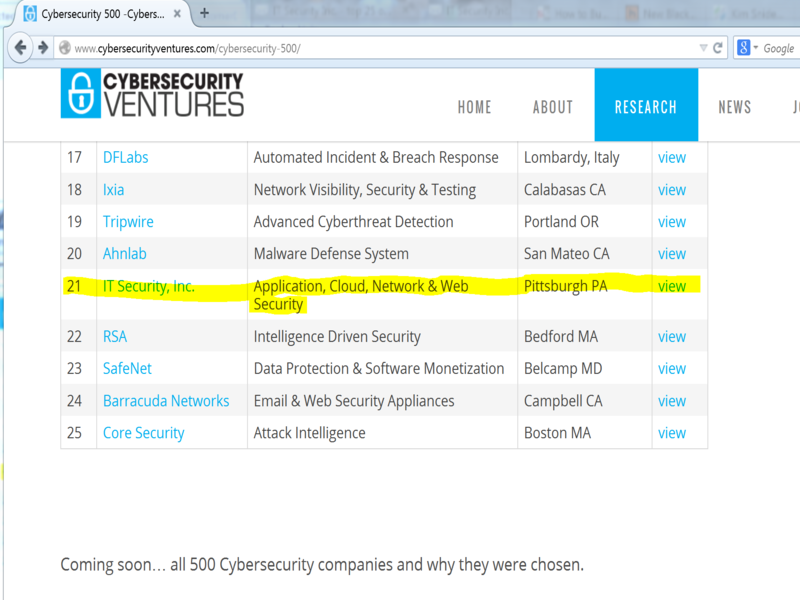
IT Security listed as #21 in the CyberSecurity 500!
Menlo Park, Calif. – October 27, 2014
Cybersecurity Ventures has announced the first annual edition of the Cybersecurity 500, a directory of the 500 hot cybersecurity companies to watch in 2015.
“We selected thousands of potential companies for inclusion in to the Cybersecurity 500, by soliciting feedback from CISOs and end-user security practitioners, visiting dozens of cybersecurity trade shows and conferences to research companies in-person, and conducting extensive online research” said Steve Morgan, founder and CEO of Cybersecurity Ventures.
The Cybersecurity 500 does not rank companies by revenues, employees, or annual growth. “We didn’t think a list of the largest cybersecurity companies would be very useful to our target audience of cyber and IT security decision makers, evaluators, and recommenders” added Morgan. “They already know who the biggest vendors are, so we are trying to create more awareness and recognition for the most innovative cybersecurity companies who they should be looking at”.
|
 |
|
Application, Cloud, Network & Web Security |
|
Pittsburgh, PA 15237 | Tel: (412) 515-3010 IT Security, Inc. is an experienced security consulting and services company with more than 25 years of Professional experience. We service clients from various fields including State and Local Government, Non-Profits, Financial, Energy & Utilities, Education, Healthcare and Manufacturing. Our security professionals are equipped to identify and re-mediate the latest hacking techniques. We are available to respond to security incidents, but really prefer protecting the enterprise before the hackers get in. As an organization, you must comply with privacy and data protection laws, regulations, and policies designed to protect confidential information, such as PCI, FISMA, GLB, HIPAA, etc. We can assist you in adopting and implementing a variety of activities related to processes and technology, without the costs of learning to implement them. Remember, being compliant, does not make you secure. Whether your needs are developing a security strategy, or assessing your organizations security posture, IT Security has professionals ready to serve your organization’s needs. |




